讲个笑话:难度,雨露均沾 :huaji22:
本篇WP只有RE
入门reverse
应该是re签到题
用IDA看关键代码:
std::operator>><char,std::char_traits<char>>(&std::cin, &v5);
for ( i = 0; i < strlen(&v5); ++i )
v6[i - 112] = (v6[i - 112] ^ 6) + 1;
if ( !strcmp(&v5, "akhb~chdaZrdaZudqduvdZvvv|") )
std::operator<<<std::char_traits<char>>((int)&std::cout, "yes!you are right");做了异或,异或后与字符串比较,直接写脚本
str1 = "akhb~chdaZrdaZudqduvdZvvv|"
key=""
for i in str1 :
key = key + chr((ord(i)-1)^6)
print key
print keyencrypt3
也没什么难度,老规矩,拉入IDA
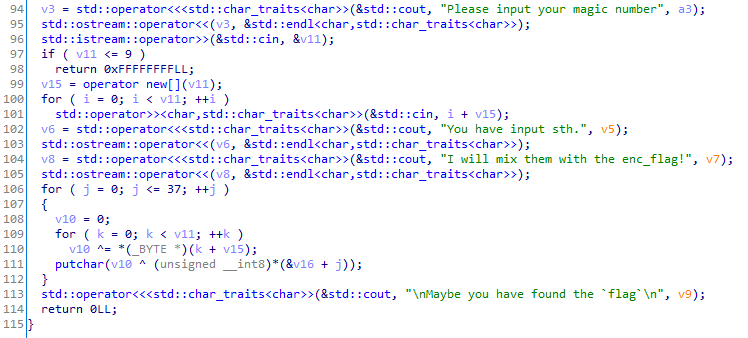
同样是做了异或算法,但是这回的异或key没有给你,但是从程序中可以看出,每一次异或的key都相同的,又已知flag的结构是flag{},所以我尝试爆破获取key
key = ord("f") ^ 38
print key
enc = [38, 44, 33, 39, 59,
35, 34, 115, 117, 114,
113, 33, 36, 117, 118,
119, 35, 120, 38, 114,
117, 113, 38, 34, 113,
114, 117, 114, 36, 112,
115, 118, 121, 112, 35,
37, 121, 61]
flag = ""
for i in enc:
flag += chr(key ^i)
print flagsm
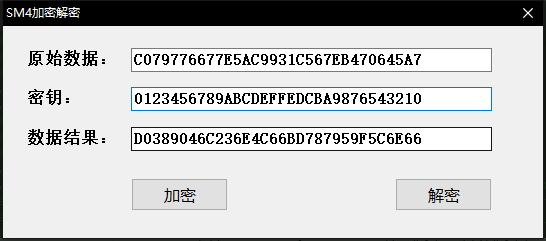
经典的SM4算法,拉入IDA后,看到定义的内容

可以看到 0x1234567, 0x89ABCDEF, 0xFEDCBA98, 0x76543210
默认的秘钥,加密后的flag是0xC0797766,0x77E5AC99,0x31C567EB,0x470645A7
用别人写的软件直接解决